Integrating Active Directory and Squid3
Here's my third and probably last post on a topic about AD integration and linux. This time around the goal is to have Kerberos authentication integrated with Squid, so that users do not have to be prompted for additional authentication when surfing the web.
The setup is the exact same as in the two previous articles (just with a 2008 DC instead of a 2003R2):
- Domain Controller and Kerberos KDC - Windows Server 2008 - dc1.win2008.corp (172.16.11.152)
- Proxy Server - Debian Squeeze (as of 05/2009) - www.win008.corp (172.16.11.16)
- Client1 - Windows XP Professional - client1.win2008.corp(172.16.11.252)
I'll assume that the AD domain is already configured and that the Debian box is already joined to the domain (see previous blog posts on how to do that). As a first step the squid3 package needs to be installed (unless #532064 is fixed you'll need to recompile the debian package with the options mentioned in the bug report):
apt-get install squid3
Then we need to export the correct keytab HTTP/www.win2008.corp as required for Kerberos authentication :
net ads keytab add -U Administrator HTTP
Once that is done we'll have the appropriate keys in the default keytab (/etc/krb5.keytab). With ktutil you can explore the keys in the file:
ktutil: **rkt /etc/krb5.keytab ** ktutil: **l** slot KVNO Principal ---- ---- --------------------------------------------------------------------- 1 2 host/www.win2008.corp@WIN2008.CORP 2 2 host/www.win2008.corp@WIN2008.CORP 3 2 host/www.win2008.corp@WIN2008.CORP 4 2 host/www@WIN2008.CORP 5 2 host/www@WIN2008.CORP 6 2 host/www@WIN2008.CORP 7 2 WWW$@WIN2008.CORP 8 2 WWW$@WIN2008.CORP 9 2 WWW$@WIN2008.CORP 10 2 HTTP/www.win2008.corp@WIN2008.CORP 11 2 HTTP/www.win2008.corp@WIN2008.CORP 12 2 HTTP/www.win2008.corp@WIN2008.CORP 13 2 HTTP/www@WIN2008.CORP 14 2 HTTP/www@WIN2008.CORP 15 2 HTTP/www@WIN2008.CORP
Make sure squid can read the keytab file: use an ACL, change file permissions or move the key to a different keytab and change the init script
KRB5_KTNAME=/etc/squid/HTTP.keytab
export KRB5_KTNAME
Here's a minimal configuration in order to test the kerberos negotiate authentication in squid (only the relevant parts):
auth_param negotiate program /usr/lib/squid3/squid_kerb_auth -d auth_param negotiate children 10 auth_param negotiate keep_alive on acl AUTHENTICATED proxy_auth REQUIRED http_access allow AUTHENTICATED http_access deny all
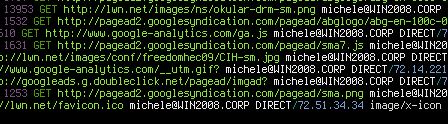
At this point a simple XP client that is joined to the Windows win2008.corp domain and that has www.win2008.corp as a proxy should be able to surf authenticated (do not forget to make sure that IE integrated authentication option is active):