Last year I reimplemented the S/Key support in gnome-terminal (#305126), and since I couldn't find the notes I took last time, I decided to setup a quick S/KEY Environment. I do recall the documentation in order to set it up was extremely scarce, so I'll try to fill in the void :)
Note: I tried going down the "recompile openssh with openbsd's skey libs", but it's too much effort to beat those libs into shape and in a way that no licenses are broken, so I'll just describe the approach using OPIE on Debian/Ubuntu.
On the server, just run:
# apt-get install libpam-opie opie-server
Then make sure that /etc/pam.d/ssh has the following in the _auth _section:
auth required pam_env.so # [1]
auth required pam_env.so envfile=/etc/default/locale
auth sufficient pam_unix.so nullok_secure
auth sufficient pam_opie.so
auth required pam_deny.so
Also make sure that /etc/ssh/sshd_config _has the setting: _ChallengeResponseAuthentication yes _
At this point, on the server, all is left to do is to "initialize" OTP. As the user wanting to take advantage of One-Time-Passwords, just run _opiepasswd -c:
Adding pippo:
Using MD5 to compute responses.
Enter new secret pass phrase:
Again new secret pass phrase:
ID pippo OTP key is 499 co9843
TEA SONG NET BONA COAT OKAY
Now OTP is correctly configured and we can focus on the client, where we'll need to install the client OTP calculator: # apt-get install opie-client, now when connecting to the just configured ssh server (leaving the first password request blank) we get our OTP challenge:
_ conrad:~$ ssh localhost
Password:
otp-md5 456 co2636 ext, Response:_
We can calculate the response to the challenge with the $ opiekey 456 co2636 command:
_
Using the MD5 algorithm to compute response.
Reminder: Don't use opiekey from telnet or dial-in sessions.
Enter secret pass phrase:
DASH IRA GWEN WAVE JUNE KEEN_
By typing _"__DASH IRA GWEN WAVE JUNE KEEN" _at the ssh password prompt we can login and not be subject to Replay Attacks . Now, this is all very nice and dandy, but it surely is rather complicated...but..enter gnome-terminal ;)
Make sure the gconf setting _/apps/gnome-terminal/profiles/Default/use_skey _is ON, login to the OTP ssh server and notice how the otp challenge is underlined when going over it with the cursor :
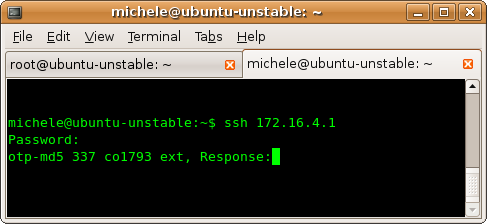
Press Ctrl-Left Mouse Button on the underlined challenge text and you'll get the following OTP calculator prompt:
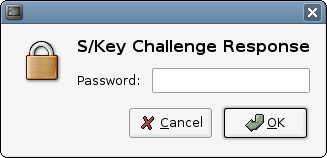
Type in your password, it will generate the correct response to the challenge and you're in ;)
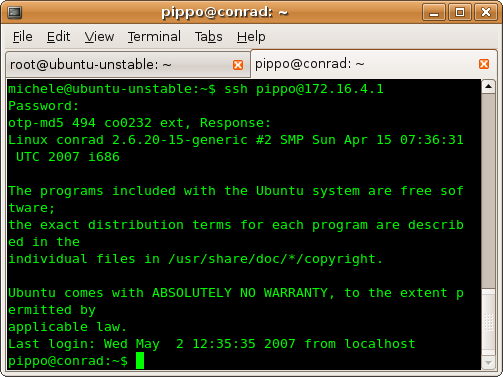
No other OTP calculators needed :)












