Putty, Active Directory and Kerberos
_Update: _This article covers pristine putty without any patches. In the past you could have obtained the same results with the many variants of putty (i.e. Quest's, Centrify's)
This is a short and simple tutorial about setting up Kerberos authentication with putty and Active Directory. Since a few snapshots putty supports Kerberos-GSS authentication on Windows. This means that we're able to authenticate, without using ssh keys and without being prompted for user/pass, to an ssh linux box which has the appropriate keys in its keytab. I covered the basics of getting the keytabs out of Active Directory onto a Linux box on my previous blog post (I am actually assuming the same setup mentioned in the previous blog posting). The linux box needs to be joined to the Windows domain via samba. Updating the keytab is then trivial; on the linux box (_www.win2008.cor_p) launch the following:
net ads keytab add -U administrator
Verify that the host/fqdn is present in the keytab list:
www:~# <strong>ktutil</strong> ktutil: <strong>rkt /etc/krb5.keytab</strong> ktutil: l slot KVNO Principal ---- ---- ---------------------------------------------- 1 2 host/www.win2008.corp@WIN2008.CORP 3 2 host/www.win2008.corp@WIN2008.CORP 4 2 host/www@WIN2008.CORP 5 2 host/www@WIN2008.CORP 6 2 host/www@WIN2008.CORP
Configure the ssh daemon on www.win2008.corp and activate the Kerberos/GSS support:
GSSAPIAuthentication yes GSSAPICleanupCredentials yes KerberosAuthentication yes KerberosOrLocalPasswd yes KerberosTicketCleanup yes
Restart ssh :
invoke-rc.d sshd restart
Once the ssh daemon is set up and the keytab contains the correct entries, we log on to a Windows XP client which has the snapshot of putty (Note: the user that logs on the Windows XP box, needs to exist on the Linux machine as well. In my case I have a "michele" user in AD, which needs to exist on Linux as well: adduser michele). We configure putty to send the system username:
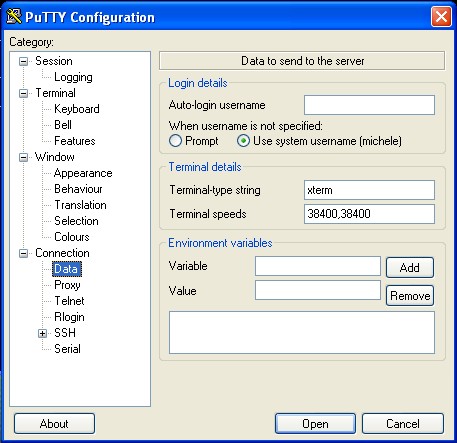
We also double check that the SSH authentication supports GSSAPI:
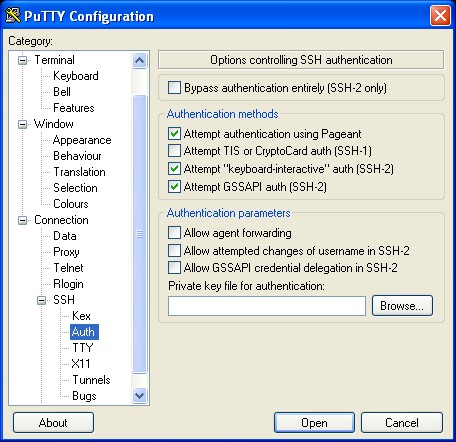
At this point we'll be ablt to login on the box from the Windows XP using Kerberos authentication (and hence making use of the TGT we get from using the Active Directory KDC):
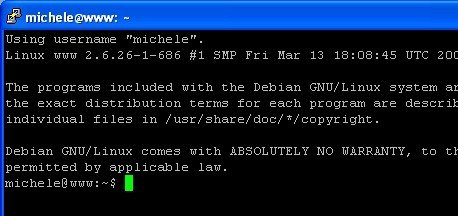
Success ;)
For the record, while logging in, sshd (at DEBUG2 LogLevel) will give the following:
May 31 15:27:36 www sshd[2757]: debug1: Got no client credentials May 31 15:27:36 www sshd[2757]: Authorized to michele, krb5 principal michele@WIN2008.CORP (krb5_kuserok) May 31 15:27:36 www sshd[2757]: debug1: do_pam_account: called May 31 15:27:36 www sshd[2757]: Accepted gssapi-with-mic for michele from 172.16.11.252 port 1117 ssh